Maintaining Privacy and Keeping Your Data Secure
There is nothing more important to us than the security of your data and keeping your information completely confidential. In today’s world, privacy is more important than ever. While some of our competitors tout their ultra secure networks as a means of keeping your data safe, we go even further. None of our data recovery servers are networked in any way, which means there cannot be a data security breach within our network at all. So none of your information will ever be shared peer-to-peer or by network intrusion.

We guarantee your data will remain 100% secured and confidential throughout the recovery process.
Data Security Compliance
 We regularly work with major health care providers, defense contractors and other organizations with highly sensitive data. We have found that each of our clients can have different requirements for their data, and they sometimes need to be guaranteed that additional measures will be taken to ensure their data security. We are more than willing to work with a company’s legal department to address any specific needs they may have. This might possibly include signing additional non-disclosure agreements.
We regularly work with major health care providers, defense contractors and other organizations with highly sensitive data. We have found that each of our clients can have different requirements for their data, and they sometimes need to be guaranteed that additional measures will be taken to ensure their data security. We are more than willing to work with a company’s legal department to address any specific needs they may have. This might possibly include signing additional non-disclosure agreements.
HIPAA (Health Insurance Portability and Accountability Act) Compliance
Working with major hospitals, healthcare providers, and medical billing companies on a weekly basis has allowed us to gain valuable experience in dealing with this sector of the market. It requires additional measures be taken to guarantee that patient data is kept completely private and secure. While we have non-disclosure elements built into the submission form that is completed when a new data recovery case is established, quite often hospitals and doctors require additional HIPAA specific forms to be signed. We have no problem working within any reasonable requirements may need to be met so that the security of your patient records is never an issue.
We also make sure that only the technician working on your recovery has access to your data. Even then, the amount of your data that is viewed is at a bare minimum. During most of the recovery process, your drive is being imaged. It is during this imaging process that we can fully view the layout of your data on your media. However, we aren’t actually viewing the files at all, we are looking at the sectors.
How We See Your Data
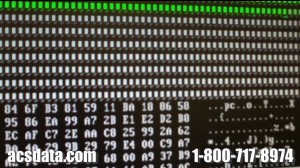 When our technicians perform your recovery, you don’t have to worry about them looking through your information. This is how we see your data. We utilize DeepSpar Disk Imagers for all of our recovery work. The Deepspar system does not use a graphical user interface, like Windows, to view the information on a hard drive. It only shows the sectors, and the raw data associated with each sector. We make 4 passes over the drive during the imaging process.
When our technicians perform your recovery, you don’t have to worry about them looking through your information. This is how we see your data. We utilize DeepSpar Disk Imagers for all of our recovery work. The Deepspar system does not use a graphical user interface, like Windows, to view the information on a hard drive. It only shows the sectors, and the raw data associated with each sector. We make 4 passes over the drive during the imaging process.
Once the imaging process is complete we will then know what areas of the drive couldn’t be read. We will make a 5th and final pass over those unreadable areas to try and read as much data as possible. After that is finished, we then mount the cloned disk to our recovery server, tree up the directory to make sure that the file structure is intact, and then begin copying the data over to the destination drive that will be shipped back to you. We may open 4 or 5 files spread out through the drive just to make sure that the files we are transferring are indeed intact. After that completes, we are done. We hold on to the cloned copy for about 10 days, just to make sure your data is received ok, and at that point the cloned drive is wiped and ready for the next recovery.
Data Security Is A Top Priority
You can rest assured that we will never do anything to compromise the security of your data. It is, and always has been, the biggest priority within our company. For over a decade now we have been recovering data for thousands of clients all over the world, and it doesn’t matter if you are a stay-at-home mom or the largest corporation on the planet…everyone gets the same treatment when it comes to keeping recovered data secure. We don’t take chances and we don’t cut corners when it comes to implementing security measures that are designed around keeping everyone’s data safe and secure at all times. If you have any questions about data security and privacy, please don’t hesitate to contact us.


